What is OTP?
One-Time-Programmable Memory (OTP) is a type of non-volatile memory (NVM), and for most applications, it is the industry standard for single-use memory.
OTP replaces Read-only memory (ROM) in applications such as IDs, production records, encryption code, etc. It is also suitable for analog trimming, function selection, and parameter setting and has been used in a broad range of applications. Since the stored data can’t be changed after being programmed, it is a fundamental element in building a Hardware Root of Trust.
There are three different types of OTP programming mechanisms that are commercially available.
- Floating gate-based OTP stores charges in its floating gate. The trapped charges can be erased by exposure to ultraviolet light or radiation, which is an advantage in specific niche markets and mature process nodes.
- eFuse OTP is based on the electro-migration effect in polysilicon or metal strips and programmed by electrically blowing a strip of metal or poly. EFuse is vulnerable to physical attacks due to visible differences between programmed and unprogrammed bits, which is dangerous when secret or sensitive data needs to be stored.
- Anti-fuse OTP is a secure OTP introduced to counter the visibility issue present in EFuse OTP. The programming mechanism in Anti-fuse OTP is based on avalanche breakdown, shorting the gate and source of a transistor. These results remain hidden, with randomized rupture spots in the oxide layer. This programming mechanism provides good data retention performance and ensures secure data storage against physical attacks, such as SEM analysis.
Safely Storing Private Keys
Key storage is often the weakest aspect of a hardware security ecosystem. It can create a clear vulnerability and immediately compromise a secure boundary if, for example, the private keys are left unsecured in eFuse. Furthermore, this can permanently weaken a chip as hardware cannot be updated after production, unlike software-based security solutions. Therefore ensuring the highest level of hardware security available should be prioritized.
The eFuse (electronic fuse) and anti-fuse OTP are the most common options for key storage in modern chip design. With eFuse, the key is programmed into the One-Time-Programmable (OTP) memory by blowing a portion of metal or poly. However, such a mechanism also leaves a visible trace in the circuitry. On the other hand, the anti-fuse OTP is programmed based on the oxide burnout mechanism. The burnout creates a conductive path without leaving any visible traces on the surface.
The image below shows both eFuse and anti-fuse OTP after being programmed and viewed from an SEM’s top view (Scanning Electron Microscope). This demonstrates how the data stored in eFuse is clearly visible compared to the anti-fuse OTP cells, which look the same when programmed and un-programmed, as the Oxide breakdown remains invisible to electron microscopy. The irreversible programming process also means it is impossible to recover from the “programmed state” to the initial/intrinsic state.
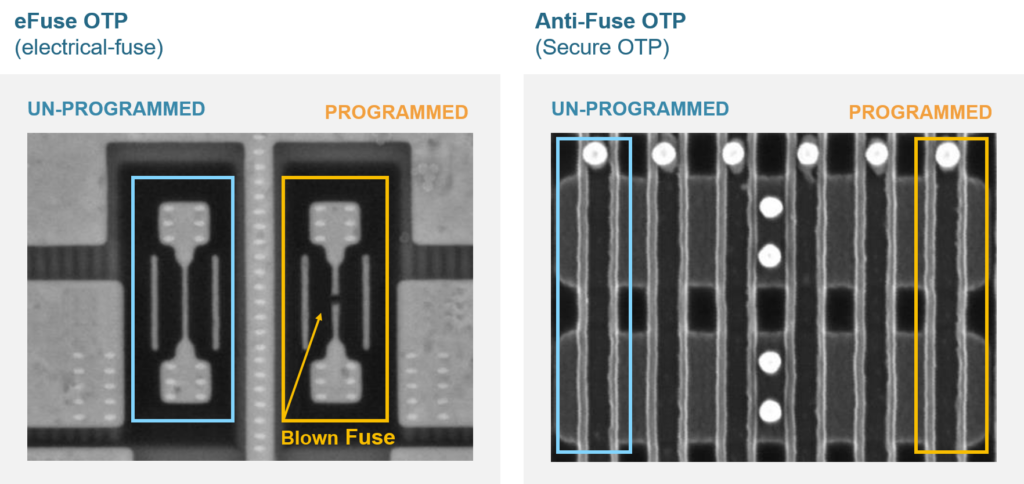
Attackers might consider alternative methods to modify the content by programming the “non-programmed” cell. However, it is not feasible for a FIB (Focused Ion Beam) attack to modify specified content at a dedicated address in the anti-Fuse OTP cell array. In comparison, FIB attack can change an eFuse cell from “0” to “1” and “1” to “0” in a more straightforward manner. Therefore, a Secure OTP anti-fuse is a better option than eFuse from the get-go.
Another key advantage of using a Secure anti-fuse OTP is that, when used in combination with a PUF’s value, the address of the stored key can be scrambled. This provides a unique randomized location for stored data on a Secure OTP, as PUF values are different from chip to chip.
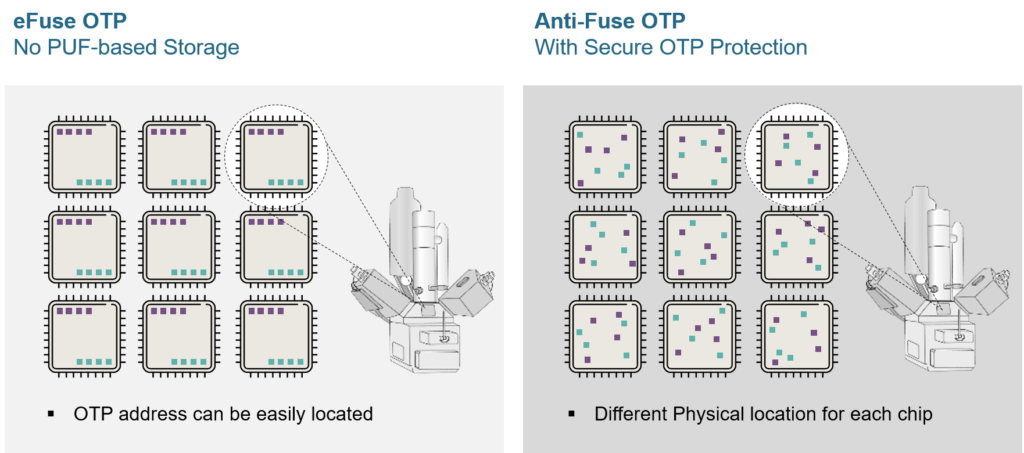
Compared with other kinds of OTP memory, anti-fuse-based Secure OTP NVM is more scalable (especially at larger capacities) while keeping read power low over a wide voltage and temperature operating conditions. Furthermore, in light of the security concerns associated with floating gate and eFuse solutions, it becomes apparent that the preferred market solution will be Anti-Fuse OTP, especially for applications such as secure key storage, device IDs, and code storage.
