Modern security depends on the five primary cryptographic functions of privacy/confidentiality, authentication, integrity, non-repudiation, and key exchange. These functions are built up from a combination of one or more cryptographic algorithms, of which many need the use of keys to operate. Hence the importance of keys to modern security cannot be overstated.
Keys are analogous to the combination of a safe. If an adversary knows the combination, the strongest safe provides no security against penetration. The experts at NIST offer their guidance on key management best practices in the SP800-57 document. Starting with a framework for thinking about key management, the publication describes the four phases (and the operations that fit within each phase) that make up the lifecycle of a key as the following:
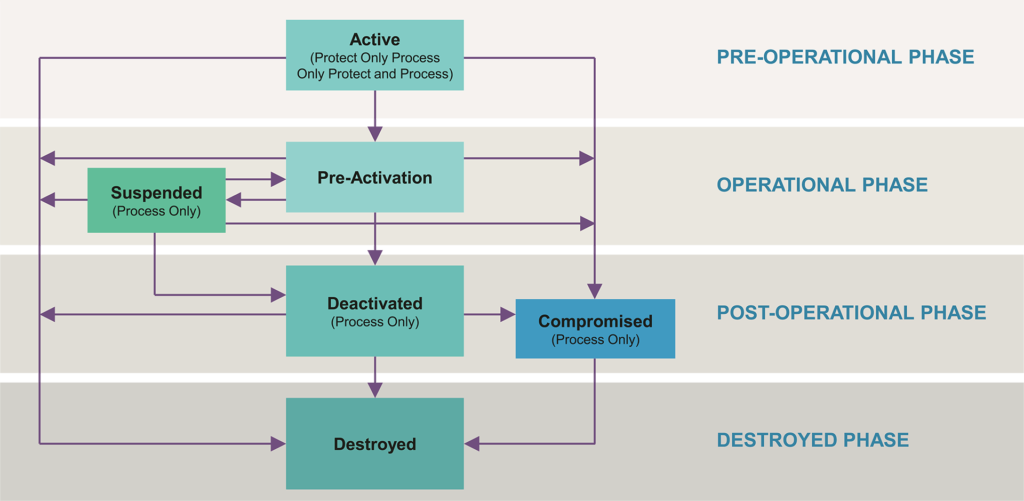
I. Pre-operational Phase
Keys are not yet ready for normal operation. They have yet to be generated or have not yet been activated/established. Key management functions during this phase are for the creation, establishment, or registration of keys in preparation for normal operations during the following operational phase.
II. Operational Phase
Keys are available for normal operation. Key management functions during this phase include key storage and the derivation of new keys from existing ones.
III. Post-operational Phase
Keys are not to be used for normal operations anymore. A key could be considered either deactivated or compromised while in this phase. Key management functions during this phase include archiving, de-registration, or destruction.
IV. Destroyed Phase
Keys are no longer available. They have been destroyed. All records of their existence may also have been deleted while in this phase. As a result, there is no need for any key management functions in this phase, as the key is gone.
Conclusion
Key management plays a critical role in modern security systems, as many of the cryptographic algorithms used in security protocols depend on keeping their keys safe. Considering the rising number of reported attacks year-over-year and the total number of companies and systems affected by each new attack, it is vitally important to have the proper key management procedures in place.
The NIST has published SP800-57 as a guide for key management, in which they have defined four distinct phases of key management. Of these four phases, three of them recommend functions to ensure the proper generation, usage, and disposal of keys in a secure setting. These recommendations outline the importance of a secure Hardware Root of Trust that combines PUF-based key Generation and Anti-Fuse OTP storage.
