What is a Hardware Unique Key (HUK)?
A Hardware Unique Key (HUK) is the device-specific key acting as the “root” of all other secret keys on a particular device. It is crucial that the HUK remains secured to maintain the integrity of the Key chain it supports.
The HUK is the root that generates multiple secret keys on a device. Therefore, it must be wholly unique, never duplicated, and unreadable by the world beyond the device.
Nowadays, there are two ways to provision a HUK; external key injection or internal key generation. However, the key injection process requires additional costs to perform key provisioning in clean rooms. In addition, the key injection procedure is vulnerable to secret disclosure and requires further external secure storage for confidentiality protection.
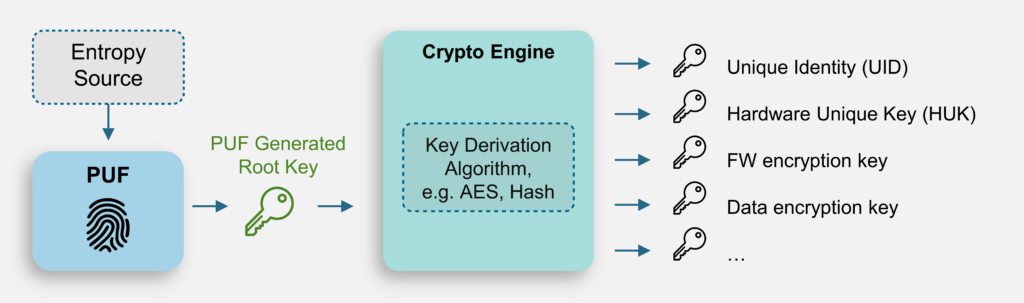
By contrast, creating HUK through internal key generation with a PUF eliminates costs associated with injection and enhances security. In addition, PUF’s two main characteristics of being random between bits and unique between chips make PUF the optimal solution for HUK generation. And by moving the entire process within the chip, the associated costs of key injection and external key management are eliminated.
While PUF can be used as a HUK directly, it can also be fed into a crypto-engine, in parallel with an entropy source such as a TRNG, to generate a HUK.
Want to learn more?
