AES: The Advanced Encryption Standard
The Advanced Encryption Standard (AES) is a symmetric encryption algorithm established by the U.S National Institute of Standards and Technology (NIST) in 2001. It is widely adopted today by governments and enterprises to protect sensitive electronic data and secure network communications.
Symmetric Key
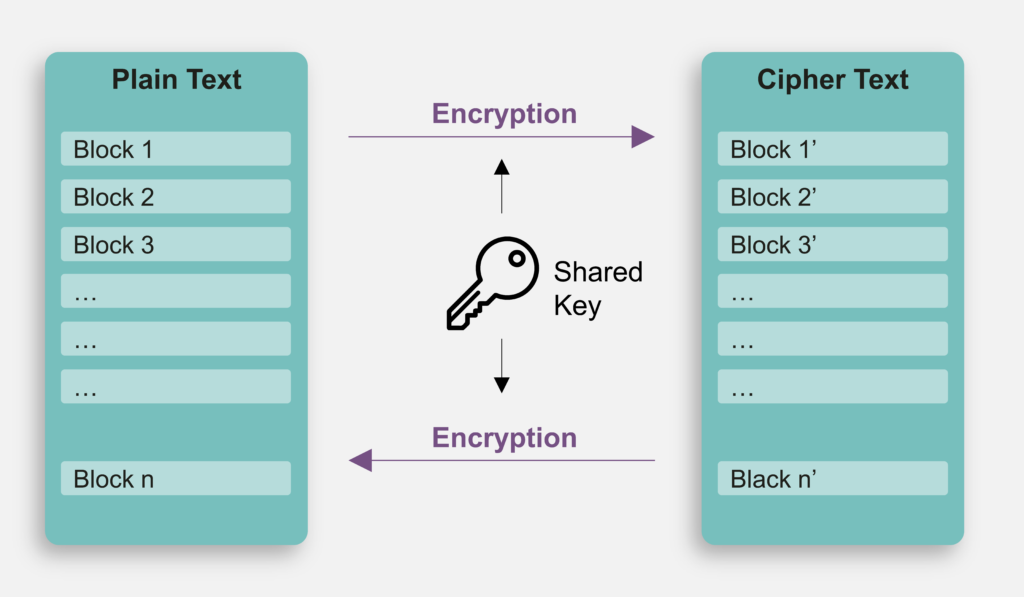
AES uses the same key to encrypt and decrypt data. This means the key used in the encryption of a piece of data is also the only key that can be chosen to decrypt that data. Additionally, the size of the AES Key can be 128, 192, or 256 bits. A larger Key size could bring more security at the cost of additional computational time.
Block Cipher
AES performs operations based on 128-bit blocks. For example, the encryption only accepts the 128-bit data as plaintext, and always generates the 128-bit ciphertext. This constraint also applies to decryption. If the plaintext size is not a multiple of 128 bits, the user should perform appropriate padding on the data before beginning encryption.
Mode of Operation
The use of block cipher itself for encryption or decryption is the trivial mode of operation called electronic codebook (ECB) mode, while the same input with the same key comes out with the same output. The cipher block chaining (CBC) mode mitigates this issue. In addition, the counter (CTR) mode uses the block cipher algorithm on successive values with the same key to produce an arbitrary length one-time pad Key for encryption and decryption. In such a way, it can support plaintext of arbitrary size.
Authenticated Encryption with Additional Data (AEAD)
Besides the modes mentioned above, AEAD is a special mode that supports the message’s authenticity. One AEAD mode is the counter with cipher block chaining message authentication code (counter with CBC-MAC; CCM) mode is used in the wireless WPA2, IPsec, TLS 1.2, etc. The Galois/Counter (GCM) mode, the most popular AEAD mode for a block cipher, is used in wireless MACsec, WiGig, Fibre channel security protocols (FC-SP), IPsec, SSH, TLS 1.2, TLS 1.3, OpenVPN, etc. It makes AES more robust and suitable for a wide range of applications.
Free Royalty
When NIST announced the request for potential AES candidates in 1997, one of the basic requirements was that the AES algorithm itself should be royalty-free. Because of this, the details of the algorithm are publicly disclosed and are in use extensively around the world.
PUFcc-provided AES Functions
PUFcc Crypto Coprocessors implements the core AES engine for block-wise encryption and decryption with a configurable number of SBOX for hardware area and performance trade-off. Furthermore, Random numbers can be introduced to the AES engine so that the masked AES calculation resists side-channel attacks. Based on the underlying AES engine, PUFcc additionally supports the ECB, CFB, OFB, CBC, CBC-CS1, CBC-CS2, CBC-CS3, CTR, CMAC, CCM, GCM, XTS, KW, and KWP modes defined in NIST SP800-38A, SP800-38B, SP800-38C, SP800-38D, SP800-38E, and SP800-38F. These implementations are all certified by NIST cryptographic algorithm validation program (CAVP).
