A PUF-based Crypto Coprocessor
PUFcc is a Crypto Coprocessor IP that combines a Hardware Root of Trust with a full suite of cryptographic algorithms, forming an adaptable security IP module suitable for integrating a wide array of system architectures. This ‘off the shelf’ solution allows designers to ‘drop and play’ a complete IP solution that enables a system’s required security protocols hassle-free.
Security on Chip has become instrumental in unlocking the full potential of IoT, AI, Automotive, and Fintech Technologies. Major incidents highlight the importance of chip security in protecting against different types of attacks throughout the product lifecycle. While software alone can only mitigate vulnerabilities to a certain degree, hardware methods establish firm foundations for device security as they expand protection starting from the design.
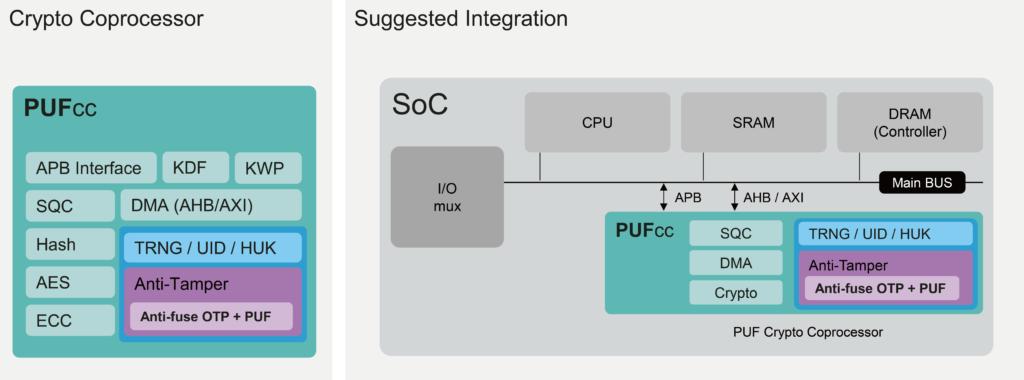
PUFcc has five main components along with their corresponding sub-blocks. The security foundation of PUFcc comes from the PUFrt Hardware Root of Trust that has our patterned PUF circuit design, which is stored in a secure OTP with an anti-tamper shell and forms the root keys. Included are the NIST CAVP-certified and OSCCA standards-compliant crypto accelerators, with ciphers, hashes, and key derivation. Individual modules control the APB and AXI interfaces, in conjunction with a direct memory access module (DMA), for faster access to external memories that must interact with the crypto coprocessor. PUFcc also has a sequencer (SQC) to spare the need for a processor or boot ROM. Finally, the optional fifth component of PUFcc is the extendable enclave to include the external Flash into the secure boundary. A list of the components and their sub-blocks can be found in the feature session and the downloadable datasheet.
By incorporating supportive crypto hardware, we arrive at a True PUF-based Crypto Coprocessor. The all-in-one integrated solution can handle all required security functions throughout the product lifecycle. Such compact design can also maintain a security boundary for keeping sensitive information or assets intact. Finally, products and services become secure as protection from the hardware level extends all the way to OS and APPs.
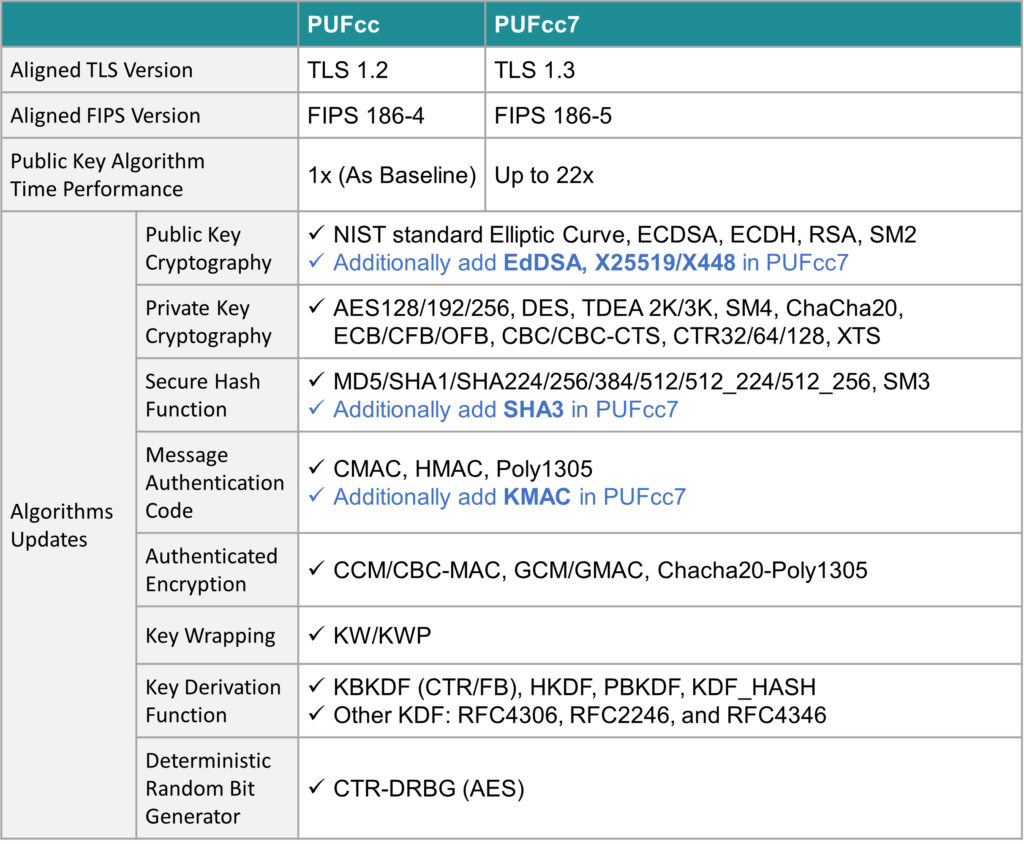
New to PUFcc Family: PUFcc7
In response to the latest TLS communication protocol TLS1.3, PUFcc7 has upgraded the PKC, SHA, and MAC algorithms, in terms of security strength and time performance.
In the PKC part, PUFcc7 added EdDSA, X25519, and X448. The time performance of the overall Public Key Algorithm has been upgraded, and there are three levels of performance settings for flexible use. Regarding security strength, it also provides four selectable PKC configurations supporting 256, 384, 521, and RSA.
PUFcc7 also adds SHA3 and KMAC to fully meet TLS1.3’s requirements. In addition, the Key Wrapping method also provides further encryption processing options on top of the original PUF scramble.
Application
PUFcc series can support the following:
- TEE security enhancement
- Key processing and generation
- Instant key wrapping or indirect key wrapping
- Key hierarchy build and advanced management
- Secure boot
- Anti-cloning and asset protection by using local key encryption
- TLS protocol
- To extend protection for external Flash
Features
- Cryptography engines supporting all elliptic curves
- NIST CAVP certified and OSCCA standards complied
- AXI or APB interface for direct memory access
- APB control interface with secure/non-secure access privilege
- Four 256-bits hardware PUF fingerprints with self health-check that could be used as a unique identification(UID) or a root key(seed)
- 8k-bit mass production OTP with built-in instant hardware encryption (customization available)
- Comprehensive anti-tamper designs in physical and RTL
- High-quality true random number generator
Additional Features
- Autoload: Automatically send trim parameters from OTP upon power-up.
- Secure Boot: Ensure the device only boots up with the authenticated software.
- Secure Debug: Ensure robust protection against potential backdoor attacks through the Debug Access Port (DAP)
Meet our experts
If you want to learn more about our PUFcc series
Meet our experts at Embedded World 2024
Evaluation Kit
If you are interested in the PUFcc, you can apply for the evaluation kit through our free evaluation program IP GO.
