The risks of an unsecured IoT
Securing the Internet of Things (IoT) is one of the biggest challenges facing the computing industry today. The IoT enables a myriad of applications, from smart homes, smart cities, smart grids, self-driven cars, supply chain logistics, automated factories, and remote health monitoring. Each of these IoT devices needs to connect and exchange data with others remotely.
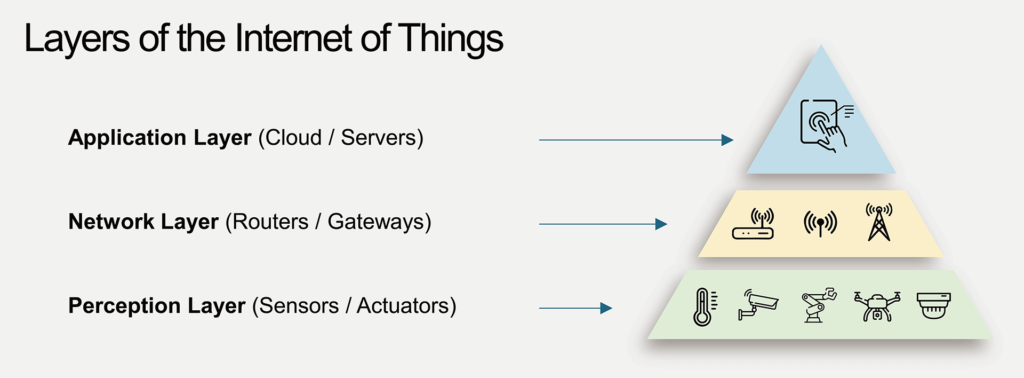
The IoT ecosystem architecture consists of three layers, all of which rely on scalable solutions for authentication and verification. The Perception Layer is the tangible real-world architecture of the IoT, where the sensors and other connected edge devices gather data. The data is then transmitted through the Network Layer, which aggregates and converts all the collected information and then shares it with other devices. Finally, the application layer represents the user interface, delivering specific services to the end-user.
However, security is a big concern in adopting the expanding universe of IoT. Therefore, Zero Trust security architecture is designed to work in conjunction with secure zero-touch IoT device deployment and enhance IoT security.
Due to the different types of attacks highlighting the importance of chip security protection throughout the entire product lifecycle, security-on-chip has become one of the critical instruments for unlocking the full potential of IoT. Zero Trust assumes that there is no security perimeter in networks, and every IoT device shall possess a security anchor: Hardware Root of Trust (HRoT), to protect against cloning, counterfeiting, tampering, and reverse engineering attacks. Hardware Root of Trust (HRoT) is the embedded building block that secures IoT devices from the ground up.
As depicted in the above figure, security at the perception layer is the foundation for security for IoT devices. An HRoT ensures secure boot, secure storage for silicon lifecycle data, and secure chip access for secure read/write data in the bottom perception layer. The network layer needs to authenticate the identity of devices, as well as support secure communication between said devices, all of which are based on the generation of security keys and unique identities. The HRoT for each device ensures a unique identity (UID) for authentication and a Hardware Unique Key (HUK) to derive the security keys necessary to protect wireless communications. In the top application layer, IoT devices need an HRoT providing an immutable secret to derive public-private key pairs for a distributed management of personal account/information on an IoT cloud server, e.g., the Fast identity online (FIDO) authentication.
A Hardware Root of Trust (HRoT) will be a requirement for each device as the foundation of a secure IoT, providing a unique, secure, and robust inborn on-chip static entropy source that is the basis for a root of trust. PUF-based silicon fingerprints are an ideal static entropy source due to their randomness, uniqueness, robustness, and non-traceability. Thus each HRoT provides a firm foundation for device security, designed from the start.
