Abstract
Data encryption can be implemented either by hardware or by software. It is generally accepted that software encryption is flexible, more cost-effective as well as easier to develop and to maintain, but it is significantly less secure and slower than its hardware equivalent. Since either hardware-based security or software-based security has its own pros and cons, a company needs to consider many factors like budget, performance, security, governing regulations, etc, to decide on choosing either hardware or software based security implementations. No matter which solution a company chose, they should be consciously aware of the “good”, “bad” and “ugly” of the solution they pick! Thus, to choose or not to choose hardware-based security is a big decision for every company to make regarding protecting their highly important sensitive information from unauthorized access. The focus of this article is on the “good”, “bad” and the “ugly” of hardware-based security.
Introduction
Data encryption has been used extensively by the governments, financial institutions, and other business to protect their highly important sensitive information from unauthorized access. There are basically two types of encryption methods that are available, namely, hardware-based and software-based encryption.
Generally speaking, hardware based encryption is considered to be safer/more secure, faster, and better assured than its software equivalent by many computer experts. However, it is also more costly, less flexible, and not easy to update or upgrade compared to its software equivalent.
This article will discuss the “good”, “bad” and the “ugly” of hardware-based security.
Preface
About 30+ years ago during a Trusted Computing conference, a 3-stars U.S. General, who was the U.S. security chief at time, used to make the following interesting remarks half-jokingly:
“I love computer hardware because I can touch it; feel about it; see it is working with my naked eyes; and best of all, I can even kick it to reboot when it breaks down!”
“On the other hand, I’m never fond of computer software because it is invisible to me; untouchable by me; hard for me to tell whether it’s really functioning; and worst-of-all I’m totally in the dark when it becomes compromised or misbehaved!”
The above remarks underlined the stereotype impressions of computer hardware vs. software and also reflected the U.S. security establishments’ preference of hardware-based security over software-based security.
What is software security?
Software-base security (or software security for short) is readily available for all major operating systems and more prevalent than hardware solutions nowadays. These software solutions can be used to protect all devices within an organization, and they are cost effective as well as easy to use, upgrade and update. They have been deployed to address basic security needs like firewalls, secure boots, PKI-based authentications, etc, to protect the devices or systems from attacks originating from both inside and outside the systems. For example, software encryption is employed to protect data at rest, in transit, and stored on different devices. However, the protection provided by software encryption solutions is only as strong as the level of security of the operating system of the host device, since any security flaw in the OS can easily compromise the security provided by the software encryption code. Furthermore, encryption software may be complicated to configure for advanced use and could possibly be turned off or by-passed by malicious users. Performance degradation is also a significant problem with software-based security.
What is hardware security?
Hardware-base security (or hardware security for short) is a discipline originated out of cryptographic engineering. It is a physical device using a dedicated security IC, or a processor with specialized security hardware specifically designed to provide cryptographic functions and also protect itself and the associated critical data against attacks. Hardware security typically contains security primitive functions such as a math accelerator, Pseudo or True random number generator (PRNG/TRNG), nonvolatile memory, tamper detection, one-time programmable (OTP) and even a physically unclonable function (PUF).
The examples of hardware security include network traffic scanner, hardware firewalls, proxy servers as well as the Hardware Security Modules (HSMs), Trusted Platform Modules (TPMs), PUFs, etc. A HSM is defined as a physical computing device that safeguards and manages digital keys for strong authentication and also provides cryptoprocessing, while a TPM is an implementation of a secure cryptoprocessor that brings trusted computing to the host system by enabling a secure environment. A PUF is a hardware one-way function realized as a physical entity that is embodied in a physical structure and is easy to evaluate but hard to predict.
Both HSM & TPM are notable implementations of the special NVM memory-based “trusted” physical computing device with expensive anti-tamper circuitry for secure key management, strong authentication and efficient cryptoprocessing. PUF is advantageous than any memory-based hardware security in terms of generating unique, unpredictable and highly secure secrets/keys for each IC inexpensively.
Why we need hardware security?
Since security operations like encryption, decryption, hashing and message authentication are executing at the IC hardware level, thus crypto algorithm performance is most likely optimized in hardware-based security devices. Furthermore, secure management of cryptographic keys is essential for the application of cryptography. In HSM/TPM, sensitive information (e.g., cryptographic keys and highly important end-application parameters) are stored in secure digital storages and protected within the security IC electronic boundary. Therefore, security ICs provide a layer of security by protecting data from unauthorized access and by preventing the exploits of specific vulnerabilities.
Traditionally computer hardware and firmware has been perceived as more dependable and trustworthy than software since the latter is susceptible to design and implementation flaws and not impervious to subversion by malicious code. Therefore, TPMs and HSMs devices have been conceived as high-assurance platforms for running critical software processes and protecting highly sensitive data against intrusion, tampering, malware, spyware, ransomware, and data leakage. Furthermore, in the 5G and IoT/AIoT era, computing devices are becoming distributed, unsupervised, and physically exposed. Consequently, attackers can physically tamper with devices which makes software-only protections inadequate and ineffective to deal with such attacks. Thus, there is a strong consensus that hardware based security solutions should be used in filling up the gaps and correcting the deficiencies of software-only protection.
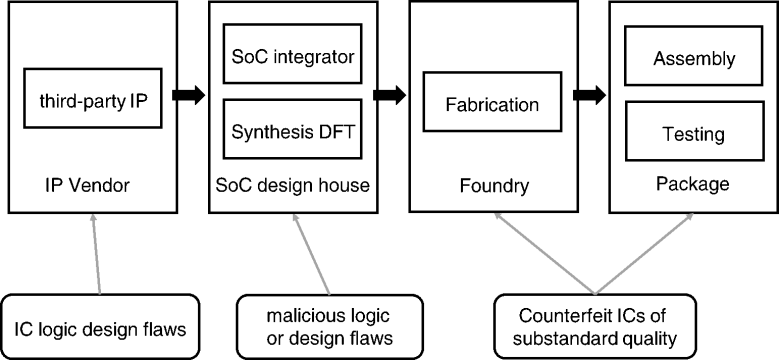
However, in recent years, the multinational, distributed, outsourcing-foundry, third-party delivered IP cores, and multi-step nature of IC production supply chain has been flooded with: 1). Counterfeit ICs of substandard quality; 2). IC logic design weaknesses and implementation flaws/defects or even hardware Trojans were introduced during physical fabrication or manufacturing; and (3). The third-party delivered IP cores may contain malicious logic and/or design flaws which could be exploited by attackers after the IP cores are integrated into SoC platforms. Based on the above security concerns and incidents, Taiwan like other advanced countries is scheduled to issue a Taiwan’s semiconductor security standards in October 2019, which is required for the entire Taiwanese IC chip production ecosystem including IC foundry, packaging,.., etc, companies during the whole life cycle of chip production to prevent any security incidents like those happened in TSMC during March 2019. It’s the “Industry 4.0” Security Standards for Taiwan semiconductor industry covering how to apply both IT&OT Security technologies to chip manufacturing ecosystem. Additionally, since third-party IP cores may become another attack vector for malicious logic insertion, the protection of pre-silicon designs by providing a dependable and trustworthy IP cores has also become equally important.
The Good of Hardware Security
Per conventional wisdom, hardware security is very effective in all application environments, especially those where the end equipment are distributed, unsupervised, and physically exposed /accessible to the adversaries. The scope of hardware security includes: hardware design, access control, secure multi-party computation, secure key storage, ensuring code authenticity, measures to ensure that the supply chain that built the product is secure, etc. Generally speaking, hardware security provides certain advantages over security by software.
Since hardware security was originated out of cryptographic engineering, there are plenty useful lessons could be learned from the comparison between the pros and cons of hardware-based encryption vs. software-based encryption. Therefore, we portray “The Goods of Hardware Security” by elaborating the “Pros” of “Hardware-based Encryption” using HSM&TPM as representative cases.
In general, the Pros of hardware-based security are as follows:
- It is safer/more secure than software encryption because the encryption process is transparent to the operating system and also separate from the rest of other processes in the host machine. This makes it much harder to intercept, tamper or break.
- It is faster than software encryption because the use of a dedicated processor which is optimized for crypto algorithm execution.
- It provides better integrity assurance than software solutions since it contains its own internally managed memory space, and its code is burnt into a chip. Thus, it cannot be tampered or modified with either by hostile content or by manual intervention.
- It uses PRNG or TRNG to generate the crypto keys and employs non-volatile memory (NVM) as the secure digital storage to store the keys along with battery powered sensors and anti-tamper package. This makes the keys inaccessible to other applications by hardware means compared to software solutions.
- In the US and EU, hardware security are required to conform or certified to internationally recognized standards such as Common Criteria (CC) or FIPS 140 to provide users with a higher level of assurance that the design and implementation of the cryptographic module and cryptographic algorithms are sound.
In summary, the good things about hardware-based security are: hardware security is significantly more secure than its software counterpart/equivalent, and the former also offers both performance and power consumption advantages than the latter. Finally, hardware security is most suitable and advisable when protecting data on portable devices (e.g., smartphone, laptop) in the distributed 5G and IoT/AIoT environments.
The Bad of Hardware Security
Ironically, the good things about software-based security are also the bad things of hardware security. Generally speaking, the cons of hardware-based security are as follows:
- It is more costly than software security since it’s using a dedicated security IC, or a processor with specialized security hardware, which may be impractical for less important applications.
- Hardware security such as hardware encryption is less flexible than its software equivalent, since it is usually tied to a particular device and one solution cannot be applied to the entire system and all its parts.
- It is not easy to upgrade and/or update hardware-based solutions compared to their software equivalents, since those functions can only be done through device substitution.
To sum up, the bad things about hardware-based security are: hardware security is more costly than its software counterpart/equivalent since it is implemented with specialized security hardware plus expensive anti-tamper circuitry; Vendor lock-in is another possible pitfall due to the fact that it could be tied to a particular device and the incompatibility with other equivalent components. Finally, the only way to upgrade and/or update hardware-based solutions is through device substitution since they are generally not re-programmable!
The Ugly of Hardware Security
Although hardware security solutions have been recognized by most security experts as more dependable and trustworthy than their software equivalents, they are not immune to IC logic design & implementation flaws or invasive & non-invasive attacks during the physical fabrication or manufacturing.
Traditional non-PUF, NVM-based hardware security approaches (e.g., HSM and TPM) for storing digital information in a device in a way that is resistant to physical attacks is difficult and expensive due to the following problems:
- Adversaries can physically extract secret keys from EEPROM while processor is off;
- Trusted party must embed and test secret keys in a secure location;
- EEPROM adds additional complexity to manufacturing.
Furthermore, attackers can extract keys from NVM while processor is off and they could also depackage, etch, and polish down to poly to read off fuse bits in order to tamper the traditional secure digital storage. Proper practices and extreme care must be taken in designing and implementing hardware security so as to avoid pitfalls that may compromise security. Otherwise, the additional risks will swamp the possible benefits of employing hardware-based security solutions. Those are the ugly parts of hardware security which must be overcome! Since PUF can generate a unique highly secure ID / secret key inexpensively, thus PUF is a holy-grail hardware security solution to remedy the pitfalls and reduce the risks introduced by current NVM-based hardware security.
Conclusion
There is neither a simple nor a single answer for a company to meet its data encryption and system integrity protection needs.
Both hardware-based security and software-based security have their own pros and cons. A company or business needs to consider factors like budget, performance, security, relevant governing regulations for data protection (e.g., HIPPA, PCI), available resources and in-house support and maintenance, etc, to decide on proper hardware-based or software-based security implementations. Therefore, no matter which solution they choose, they should be consciously aware of the “good”, “bad” and “ugly” of the solution they pick!
In summary, due to the recent publicized worldwide cyber-attacks on both public and private sectors and skyrocketing malware infections on IC production supply chains, as well as more and more stringent security regulations and protection requirements (e.g, GDPR, HIPPA, PCI), we need an effective, efficient and resilient security solutions in the IoT/AIoT/5G eras. Based on the previous discussions, we are positive that hardware based security is indeed safer/more secure, faster, and better assured than its software equivalent. Furthermore, hardware based security is very effective in all application environments, especially those where the end equipment are distributed, unsupervised, and physically exposed /accessible to the adversaries, such as the distributed 5G and IoT/AIoT environments.
Therefore, it becomes more and more apparent that a hardware security based solution is not only a “must” but also a “preferred” choice for an enterprise for the protection of their highly important sensitive information and their supply chains from cyber attacks.
Reference
- https://en.wikipedia.org/wiki/Hardware_security
- https://en.wikipedia.org/wiki/Hardware_security_module
- https://en.wikipedia.org/wiki/Trusted_Platform_Module
- https://community.spiceworks.com/topic/2167216-the-future-of-incident-response-bruce-schneier-keynotes-spiceworld
- Wayne Burleson ; Onur Mutlu ; Mohit Tiwari, “Invited: Who is the major threat to tomorrow’s security? You, the hardware designer”, published in 2016 53nd ACM/EDAC/IEEE Design Automation Conference (DAC), 5-9 June 2016.
- Daniel Brecht, “Tales from the Crypt: Hardware vs Software”, Infosecurity Magazine, 6/23/2015
https://www.infosecurity-magazine.com/magazine-features/tales-crypt-hardware-software/
