The semiconductor supply chain is vulnerable to hacks that threaten valuable intellectual property and the operation of electronic devices that we depend on. This article outlines how a combination of Physical Unclonable Function (PUF) + blockchain + smart contract technology can help safeguard the industry.
Semiconductors are vulnerable to non-invasive attacks such as side-channel analysis, Hardware Trojans and invasive/semi-invasive attacks that enable tampering and reverse engineering. However, nowadays, chip supply chain integrity is in the headlines because products from untrusted sources pose far-reaching and expensive security risks.
Bad chips may be counterfeited, modified, recycled or re-marked for reasons that include fraud and industrial espionage. Electronics made with counterfeit chips endanger critical applications for avionics, transportation systems, industrial control, IoT, 5G and defense.
Moreover, these compromised chips cause financial losses and reputational damage for manufacturers caught in a bad supply chain.
PUF “Fingerprints”
Chip IDs can help screen out counterfeit devices before assembly and during failure analysis [1].
A root of trust (RoT) is a set of ID functions in hardware that are trusted by a device’s operating system. A RoT contains keys used for cryptographic functions and enables a secure boot process.
A PUF works like a “fingerprint” providing a unique identity for a semiconductor with tamper-proof qualities for secure authentication. As an excellent source of high entropy, a PUF can generate a unique intrinsic identity that’s effective throughout the life of a chip. A PUF can provide a strong RoT for security measures (e.g., firmware signing or secure boot), as well as device identification/authentication to assure a given chip/device is genuine. For this reason, PUFs promise to mitigate supply chain attacks [2].
Blockchain
Consortium blockchain and Ethereum smart contract technologies can identify and track procured parts along the supply chain [3]. Over the lifetime of an IC, ownership transfer information is recorded and archived in a blockchain used as a public immutable database. PUFs work as tamper-resistant IDs to help identify parts via blockchain.
This proposed solution automates hardware and software protocols using a blockchain-powered smart contract that authenticates, tracks, analyzes and provisions chips throughout their life cycle.
PUF + blockchain can create trust, traceability and proof of provenance across the supply chain.
NeoPUF + Blockchain + Smart Contract
NeoPUF intellectual property (IP) from eMemory/PUFSecurity uses irregular oxide properties created during the chipmaking process as an entropy source to create the unique identity of a semiconductor [5].
NeoPUF can generate uniquely random sequences for IDs in applications with high security requirements. This IP enables multi-layered security and eliminates the need for a costly and complicated ECC (error correction code) that’s typical with other PUF solutions.
Random numbers from NeoPUF are unique and unclonable, silicon “fingerprints” supporting security measures including encryption, identification, authentication and key generation.
NeoPUF performs well using PUF qualification and performance metrics. The IP has enhanced security because it can prevent attacks used on memory-based PUFs. NeoPUF is an elegant root-of-trust for chip-level security [6,7].
For chip registration and authentication, a PUF can generate challenge-response pair (CRP) data with a smart contract . This can effectively solve compromised-chip issues by registering a CRP on a blockchain during the chipmaking process that can later authenticate products containing PUF IP.
CRP data/tables can be saved in on-chain or off-chain storage (e.g., InterPlanetary File System (IPFS) hash-tree structure) during the chipmaking stage, and a App mobile client application can be developed to simplify registration and authentication.
PUF’s CRP data works with a blockchain smart contract for on-chain and off-chain data linkage to ensure end-to-end data integrity using PUF anti-cloning data, blockchain and off-chain IPFS storage.
In [3], a pseudo smart contract with a Github source code repository are provided for reference. Reference [8] suggests using an ERC721 non-fungible token (NFT) smart contract to add supply-chain traceability. With these two approaches, we propose to tokenize each chip component as an NFT with PUF as a chip fingerprint.
For example, Cryptokitty, a popular ERC721 application, adds Kitty’s DNA sequence as a 256-bit number. Similarly, PUF can replace the DNA in a ERC721-based smart contract.
Open standard and open source, ERC721 is supported by Ethereum communities such as OpenZeppelin and has predefined Ethereum Solidity interfaces for inheritance, so in developing a smart contract for registerIC(), registerComponent(), registerDevice() as described in [3], we can add PUF CRP data to the ERC721 smart contract framework during the ERC721 token-creation process, and thereby limit the total supply of chips to prevent unauthorized overproduction.
ERC721 has well-defined ownership functions for NFT token transfer as described in [8]. If necessary, a finite-state machine in the smart contract during the chip making process can enhance the granularity of traceability [9].
Implementing PUF CRP in an ERC721 smart contract is easier today as Ethereum Smart Contract-development communities have created various development tools.
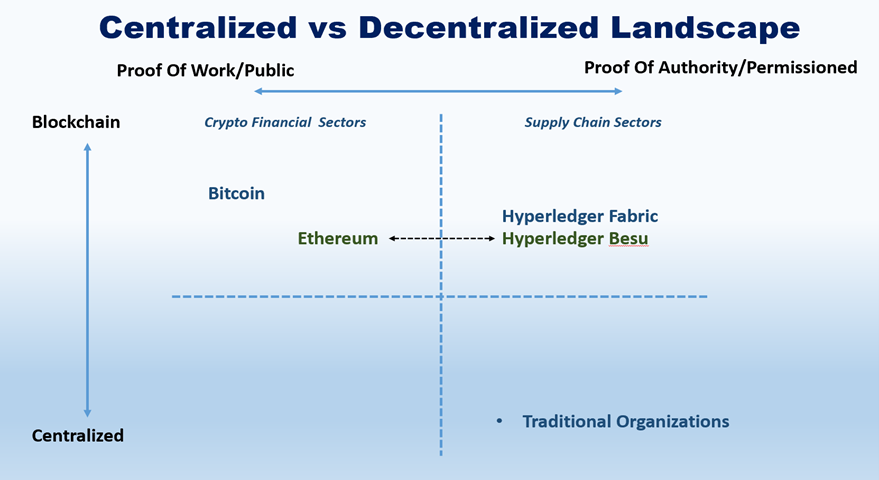
However, using public Ethereum for supply chain management is inefficient due to its Proof of Work consensus mechanism. Both [3] and [8] address these issues and recommend permissioned-blockchain.
The primary focus of Hyperledger is an open-source enterprise-grade permissioned blockchain system. Hyperledger Fabric became active in 2019 in supply chain logistics for enterprise blockchain.
Hyperledger Besu implements the Ethereum protocol [10], is compatible with Ethereum and can run the Ethereum public main net or consortium permissioned chain by replacing Ethereum public chain’s Proof of Work consensus mechanism with Proof of Authority (Figure 1) to improve transactions per second (TPS) and enable privacy features for distributing private transactions to involved participants.
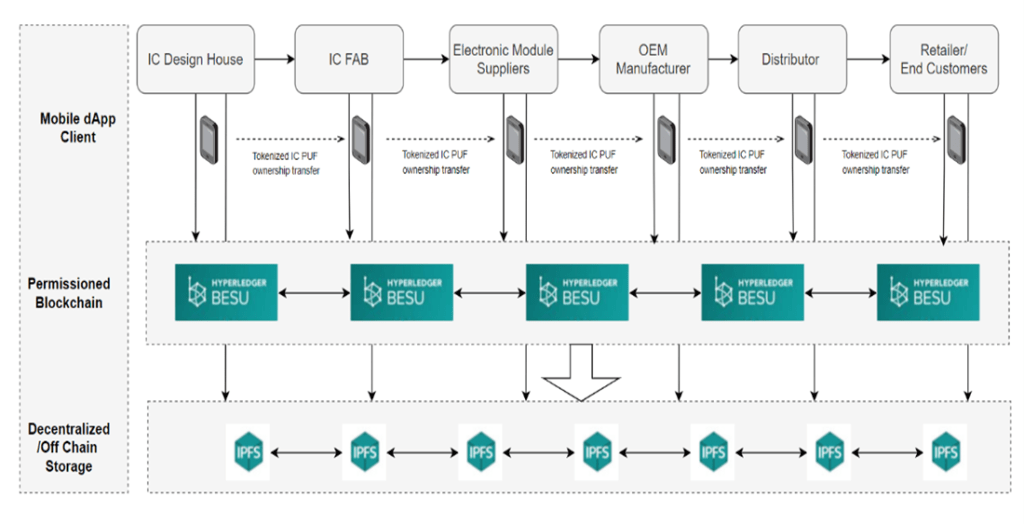
A chip can be traced from its design to final use (Figure 2). A chip designer can develop and deploy a smart contract to the Hyperledge Besu consortium chain by setting a maximum number of semiconductors to be made by a chip foundry. The chip designer executes a smart contract that records each chip’s PUF CRP data via blockchain. Once the production limit is reached, the foundry will not be able to record new CRP data to the smart contract.
In summary, our PUF fingerprint that’s stored with blockchain can verify and trace goods in a supply chain elegantly, thereby helping to resolve chip counterfeiting and overproduction issues.
Recommendations
NeoPUF + Blockchain + Smart Contract work effectively to mitigate threats to the chip supply chain in the following staged approach:
- Track provenance
- Adopt blockchain + smart contract to ensure transparency and traceability
- Use a PUF-generated “fingerprint” to resolve chip counterfeiting and overproduction issues
We at PUFsecurity provide NeoPUF technology as a root of trust to secure semiconductor, IoT and 5G supply chains. PUF-based solutions for the semiconductor supply chain can defend from deliberate attacks that compromise chip IP and trade secrets.
References
- Bryon Moyer, “New And Innovative Supply Chain Threats Emerging”, SemiconductorEngineering, November 5th, 2020
- Albert Jeng, “PUF is a Hardware Solution for the Sunburst Hack”, 01.25.2021, DESIGNLINES, EETimes. PUF is a Hardware Solution for the Sunburst Hack | EE Times
- Md Nazmul Islam and Sandip Kundu “Enabling IC Traceability via Blockchain Pegged to Embedded PUF”, ACM Trans. Des. Automatic. Electron. Syst. 24, 3, Article 36 (April 2019)
- Hsu, Charles, “SRAM PUF is Increasingly Vulnerable”, ChipEstimate.com, March 17, 2020, SRAM PUF is Increasingly Vulnerable — eMemory Technical Article | ChipEstimate.com
- Hsu, Charles, “PUF Series 2: NeoPUF, A Reliable and Non-traceable Quantum Tunneling PUF”, ChipEstimate.com June 2, 2020. PUF Series 2: NeoPUF, A Reliable and Non-traceable Quantum Tunneling PUF — eMemory Technical Article | ChipEstimate.com
- PUF: A Crucial Technology for AI and IoT (design-reuse.com)
- Run by Chips, Secured with Chips – Hardware Security with NeoPUF solutions (design-reuse.com)
- Tracing manufacturing processes using blockchain-based token compositions Martin Westerkamp *, Friedhelm Victor, Axel Küpper Service-centric Networking, Telekom Innovation Laboratories, Technische Universitat Berlin, 10587, Berlin, Germany
- Designing Secure Ethereum Smart Contracts: A Finite State Machine Based Approach, December 2018 https://www.hyperledger.org/use/besu
