The security of AIoT devices has become increasingly important. In order to ensure that the system’s security functions are working effectively and protecting every node and edge device from information security risks, it is important to generate a unique root of trust in the security system rooted in the chip. In addition to the traditional pre-injection key method, the use of a natural root key, PUF (Physical Unclonable Function), is the latest advanced solution that provides a higher level of protection in the production process and chip security. The security and reliability, as well as the design planning and mass production of the overall security module need to be taken into consideration when integrating PUF into chip designs. In this article, we will use NeoPUF as an example to discuss the issues that might be encountered when using PUF.
I. Randomness
NeoPUF creates entropy in two parallel transistors based on quantum tunneling mechanism (Refer to PUFSeries 3). The concept is like flipping a coin to determine the chances of heads and tails. The high voltage will be applied to NeoPUF until one of the oxides begins to have a tunneling current which determines an output value of either 0 or 1. Since each bit is an effective static entropy, NeoPUF can easily achieve an entropy pool of any capacity. We could exam the randomness of NeoPUF by using the min-entropy analysis from NIST 800-90B; its value is 0.988 and perfectly fits the IID characteristics. On the other hand, SRAM PUF often has process dependency problems, such as even-odd bit lines, even-odd word lines, or special dependencies (WL/BL Even-Odd or Pattern effect), which are unavoidable in the semiconductor manufacturing processes. SRAM PUFs also requires additional pre-screening and post-processing procedures for error correction.
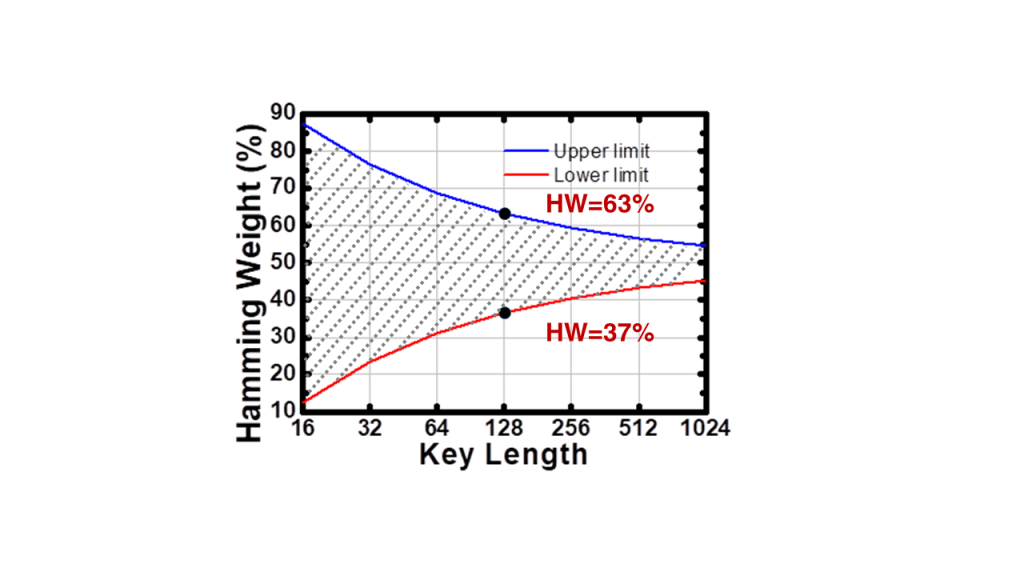
How do you judge whether a PUF is truly random? Is it affected by sample size? Figure 1 illustrates the relationship between Hamming Weight (HW) and key length. The area between the blue and red curves represents a reasonable HW (3sigma confidence level) distribution. Using a 128-bit key length as an example, there is a 99.7% chance that the samples will obtain a hamming distance of 37% to 63%.
Based on this theory, examining PUFs from a different perspective will lead to an interesting question given that a 128-bit PUF value is arbitrarily obtained, can we determine whether the PUF is truly random or non-random based on the Hamming weight result? The answer is hard to judge. Obviously, the PUF length is too short and the entropy pool is too small. Therefore, it impossible to obtain effective min-entropy analysis and effectively evaluate whether the sequence is truly random or not. In contrast, if the PUF entropy pool of each chip is 2048 bits or higher (such as NeoPUF), the randomness can be easily evaluated by statistical sampling methods, allowing it to be easily implemented in the chip.
II. True Hardware
A true hardware root of trust is preferably created from pure hardware. If it uses a PUF that requires software assistance (such as SRAM PUF), there are several hidden caveats:
- Test cost: PUFs that require additional software and firmware support usually need more test time. The general quality test is conducted by the JTAG channel, but software and firmware cannot be activated at this point. You need to wait for the CPU to assist in completing the test which will increase the testing cost and lower the throughput.
- Security vulnerabilities: the security boundary includes a processor (CPU), firmware, and software. These three are the most difficult components for a security chip to handle and have many vulnerabilities for side channel attacks.
- Design flexibility: error correction and voting combination circuit purely operated by hardware design is very common. However, what if the error rate exceeds expectations and cannot be repaired in the production process or market application? It will lower production yield and cause subsequent return problems.
For NeoPUF, which is generated by pure hardware, both the entropy source and the original key can be prepared in micro-sec. It does not require additional software support, thereby reducing test time and system security risks, as well as making it relatively easy to design into chips.
III. Security
Complete security must fully consider the system’s ability to resist invasive, semi-invasive, and non-invasive attacks during the power-on and power-off stage.
Power-Off: The principle of generating NeoPUF is based on creating an entropy source caused by a current tunneling through the gate oxide. In other words, there is no actual key information stored and therefor no physical traces. Of course, the design layout including the arrangement of the element array and the related circuit require a complete design set to ensure the reliability of the overall security mechanism.
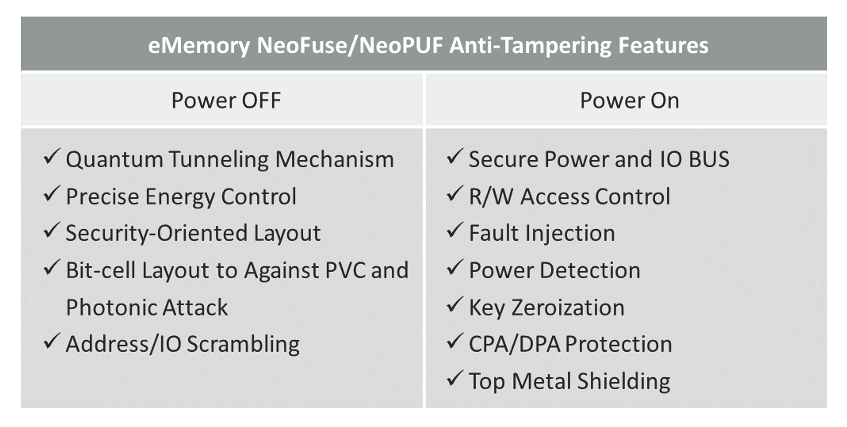
Power-on: During the key generation process of the entire security module, it is necessary to strengthen the electrical protection when reading PUF value. Hackers may attack the system by targeting or using data IO, control signal, and power consumption analysis. That is why a complete high-standard security design should include the features and function designs as shown in Table 1.
Table 1. The Anti-Tampering Features of NeoPUF
IV. Mass Production
“Security” should not only be regarded as an “added value”. Even if the security functions only occupy a small area in chip deployment (<0.1mm2), its yield performance and life cycle are also important. Therefore, PUF must be able to ensure that the bit error rate is greatly reduced in the pre-screening process during the mass production stage. Furthermore, the test process must ensure that the range of the bit error rate under various temperature, environment, and process variations are within the capability of the error correction circuit. It is necessary to predict the changes of the bit error rate of the entire component in the product life cycle. A PUF-based security design should not only be a “function”, but also a complete product that promises yield and reliability so that we could say it meets the qualification to proceed to the mass production.
In conclusion, the complete security designs of eMemory’s NeoFuse and NeoPUF have passed third-party security certifications, which also ensures that clients can enjoy high security performance and yield during mass production. We believe that only when clients really apply the complete security design to mass-production and product applications can there be a win-win situation for IP suppliers and SoC manufacturers.
V. Reference Materials and Sources
[1] PUF Series 1: SRAM PUF is Increasingly Vulnerable
[2] PUF Series 2: NeoPUF, A Reliable and Non-traceable Quantum Tunneling PUF
[3] PUF Series 3: The Quantum Tunneling Mechanism of NeoPUF
[4] PUF Series 4: Why a True Hardware PUF is more Reliable as RooT of Trust
[5] PUF Series 5: PUF based Root of Trust PUFrt for High-Security AI Application
[6] Wu, M. Y., Yang, T. H., Chen, L. C., Lin, C. C., Hu, H. C., Su, F. Y., … & Yang, E. C. S. (2018, February). A PUF scheme using competing oxide rupture with bit-error rate approaching zero. In 2018 IEEE International Solid-State Circuits Conference-(ISSCC) (pp. 130-132). IEEE.
For more information of PUFsecurity, please visit www.pufsecurity.com
