PUF stands for “Physically Unclonable Function” and is a physically derived “fingerprint” that serves as a unique identity for semiconductor devices. Their properties depend on the uniqueness and randomness of the physical factors induced during the manufacturing stage of a chip. These physical variations are unpredictable and unclonable; that’s why PUFs are suitable to serve as a root of trust with security functions in devices. In practice, we could transfer those microvariations of PUFs into sequences that consist of 0 and 1 in order to be used as keys, identities, or nonce for advanced security functions.
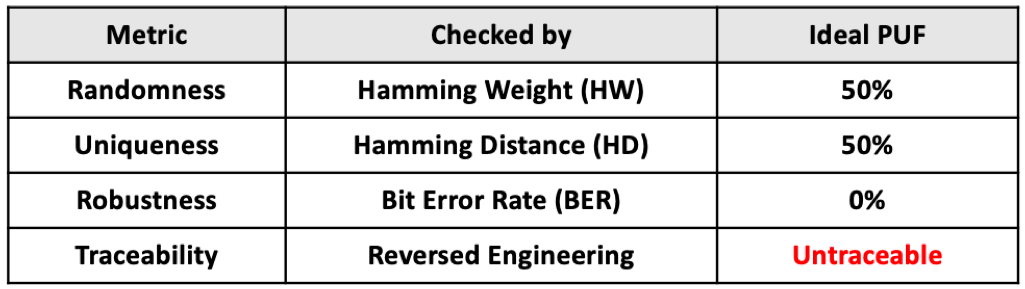
Since there are many ways to produce PUFs, there will also be many differences in its performance. Generally, PUFs can be evaluated by four dimensions including randomness, uniqueness, robustness and traceability as defined below:
- Randomness: PUFs depend on random physical factors introduced during manufacturing. The value derived from each PUF should be unpredictable, or at the very least, very hard to predict. Statistically, an ideal PUF will have a hamming weight of 50%, meaning that there is an equal number of 0’s and 1’s in the set of values, which makes the sequence the hardest one to guess.
- Uniqueness: PUFs depend on the uniqueness of physical microstructure, which are expected to be different from each other or have the lowest chance of collision. Similarly, we use hamming distance to measure the difference between two sets of values in strings of the same length. For an ideal PUF, a 50% hamming distance indicates that between any two strings, half of the numbers remain the same while the rest are different. That would lower the chances of collision between any two strings.
- Robustness: PUFs must be very stable and reliable to retain its number for the whole lifetime. This means that PUFs can maintain their stability so that the 0 and 1 in a sequence won’t be reversed even under drastic environmental changes. In other words, an ideal PUF should have a bit-error-rate of 0% to prove its stability.
- Non-traceability: As the root of trust, PUF needs to be resilient to physical attacks. Non-traceability is an important feature of an ideal PUF. That is, the random number in the PUF should not be detected and extracted by any means, such as reverse engineering, charge residue measurement, etc.
SRAM PUF vs. NeoPUF: Mechanism and Performance Comparison
Here is an example of the comparison between two well-known PUFs in the current market: SRAM PUF (Intrinsic ID) and NeoPUF (PUFsecurity/eMemory).
An SRAM PUF is enabled by the local mismatch between the threshold voltage in a pair of MOSFETs to generate a positive feedback loop. The slight differences caused by the mismatch characteristics will be amplified and divided into 0 or 1 and stored in SRAM. A random value of either 0 or 1 results from the variations of the threshold voltage in the MOSFETs.
However, the stability of an SRAM PUF’s extracted random value is seriously impacted by the following factors:
- The degree of mismatch: As semiconductor process technology continues to advance, the degree of mismatch in a pair of MOSFETs becomes smaller, causing the latched position (random value 0 or 1) in the SRAM to be flipped over easily when the SRAM is reset.
- Variations of ambient conditions: Variations in ambient conditions such as temperature, noise, voltage, and interference will possibly cause changes in the random values extracted from the SRAM.
(For a more detailed explanation of SRAM, please refer to SRAM PUF is Increasingly Vulnerable)
NeoPUF, invented by eMemory, is a PUF that extracts the variations in the quality of intrinsic oxide to become a unique signature. It is a well-known fact that there are many silicon and oxygen dangling bonds (oxide traps) in the gate oxide which act as a leakage pass for electrons. As the gate oxide gets thinner, the electrons can tunnel through the thin oxide easily. It is also known that if the electrons gain enough energy, they can break si-o bonds and create more dangling bonds (oxide traps) that enhance the electron tunneling. ([Ref] Hsu, C. C. H., & Sah, C. T. (1988). “Generation-annealing of oxide and interface traps at 150 and 298 K in oxidized silicon stressed by Fowler-Nordheim electron tunneling.” Solid-State Electronics, 31(6), 1003-1007.)
As a result, we can take advantage of these intrinsic microstructure differences to create the PUF number. To do so, we need to apply a high electrical field to two adjacent transistor gates in parallel to see which one has the higher quantum tunneling current. A higher current occurs first due to more dangling bonds (oxide traps). By repeating this process for many pairs of transistor gates, we can create a PUF random number since we never know where we will see the high quantum tunneling current among the two gates. This is like tossing a coin, the chances of heads and tails are 50%. In addition, the dangling bonds of silicon or oxygen cannot be reconnected easily at a temperature below 700C.
The tunneling current of the structure will remain over the lifetime of the devices. The microstructure changes in the oxide property cannot be detected using FIB (Focused Ion Beam) on SEM (scanning electron microscope) or TEM (Transmission electron microscopy) samples. This undetectable feature makes the secret in this PUF is physically untraceable. Consequently, this PUF meets the four important characteristics of an ideal PUF.
Thus, compared to SRAM PUF, the value of a NeoPUF is unlikely to be affected by environmental conditions or physical aging issues. Furthermore, PUFsecurity developed a PUF-based true random number generator which is adapted from NeoPUF and has passed the full NIST 800-22 test. The NeoPUF is also silicon-proven and meets an outstanding reliability performance of 0 error bit rate. In addition, NeoPUF also demonstrates impressive statistical results in Hamming Weight and Hamming Distance, which indicate the ideal randomness and uniqueness. The comparison of NeoPUF and SRAM PUF is summarized in the following table.

*Reference: Wu, M. Y., Yang, T. H., Chen, L. C., Lin, C. C., Hu, H. C., Su, F. Y., … & Yang, E. C. S. (2018, February). A PUF scheme using competing oxide rupture with a bit-error-rate approaching zero. In 2018 IEEE International Solid-State Circuits Conference-(ISSCC) (pp. 130-132). IEEE.
**Reference: Claes M., van der Leest V., Braeken A. (2012) Comparison of SRAM and FF PUF in 65nm Technology. In: Laud P. (eds) Information Security Technology for Applications. NordSec 2011. Lecture Notes in Computer Science, vol 7161. Springer, Berlin, Heidelberg
***Reference: R. Maes, V. Rozic, I. Verbauwhede, P. Koeberl, E. van der Sluis and V. van der Leest, “Experimental evaluation of Physically Unclonable Functions in 65 nm CMOS,” 2012 Proceedings of the ESSCIRC (ESSCIRC), Bordeaux, 2012, pp. 486-489.
Usage of PUF: Take NeoPUF as an Example
Not only does NeoPUF have advantages with its robust performance, its usage is widespread too. For example:
- Securing Storage NeoPUF can be used as the invisible key for protecting injected secrets which are essential for IoT devices when the shared key is stored inside the IoT chip.
- Inborn Root of Trust NeoPUF’s inborn root of trust can also allow it to become the unique key for security functions. It’s inborn randomness and uniqueness is ideal for UID, especially since NeoPUF is qualified with a lifetime zero bit-error-rate. Its on-demand keys also make it perfect for on-chip secret and off-chip ID generation.
- The ideal static entropy source of tRNG NeoPUF is a good seed for random number generation. For example, PUFsecurity uses NeoPUF as a static entropy to develop PUFtrng with its own logical designs. The PUFtrng features ultra-fast initial time (ready in m-sec), high-speed throughput (over 100Mbits/sec) and low power consumption (lower than 1pJ/bit), which is suitable for lightweight and cost-effective IoT devices. More impressively, the quality of its true random number bits passed the NIST SP 800-22 test and 800-90B compliance criteria.
- The Wide extension of PUF-based hardware security IPs PUFsecurity will continue to publish article series to discuss PUF-based hardware security in the future.
For more information, please visit www.pufsecurity.com and www.ememory.com.tw
